前言
当企业需要透过 Internet 使用 Routing Protocol 进行 Route 交换时,通常会在 Site 与 Site 之间建立 GRE Tunnel。但 GRE Tunnel 并无加密功能,流经 Internet 的资讯变得不安全,这时候 GRE 可与 IPSec 一起应用。本文会介绍两种非常相似的技术,分别是:GRE over IPSec 及 IPSec over GRE。阅读本文前读者需掌握 IPSec VPN 设定,及对 EIGRP 有基本认识。
基本理论
假设两地 Router 已连接 Internet 并有 Static IP Address,能互相 Ping 通,现想透过 EIGRP 交换 LAN Subnet 的 Route。然而要建立 EIGRP Neighbor,两只 Router 需要拥有位於相同 Subnet 的 Interface,此时网管人员必然想到要做 GRE Tunnel。馀下的问题是先做 GRE Tunnel 再在里面做 IPSec Tunnel 加密?还是相反,先做 IPSec Tunnel 加密後再在里面做 GRE Tunnel?
GRE over IPSec
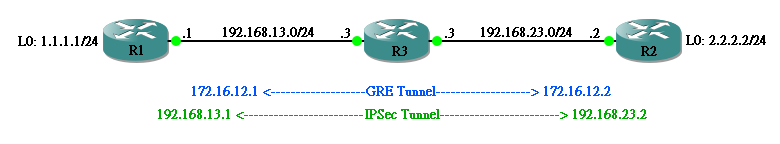
第一个方法是 GRE over IPSec,即 IPSec 在最外层(或称最底层)。意思是先在 R1 与 R2 之间建立 IPSec Tunnel,把里面的 GRE Tunnel 整个进行加密,Routing Protocol 在 GRE Tunnel 里面完成 Route 交换,最後 Data 在 GRE Tunnel 里面传送。从下图所见,因整个 GRE Tunnel 被加密,所以里面的 Routing Protocol 及 Data 都会被加密。

IPSec over GRE
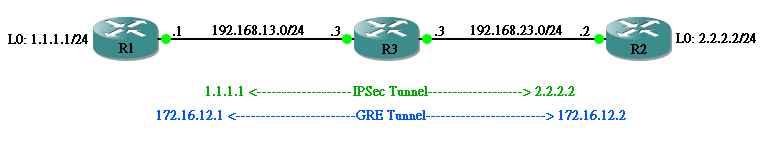
另一个方法是 IPSec over GRE,即 GRE 在最外层(或称最底层)。在 R1 与 R2 之间先建立 GRE Tunnel,在 GRE Tunnel 里面再建 IPSec Tunnel,有趣的是:由於 IPSec 并不支缓 Multicast,因此通常把 Routing Protocol 建在 GRE Tunnel 进行 Route 交换,并无加密,只有 Data 在 IPSec Tunnel 里面被加密。如坚持把 Routing Protocol 也放在 IPSec Tunnel 中,可以透过设定 Unicast IP Address 建立 Neighbor,但这样做 Router 就无法自动建立 Neighbor 关系,如果 Router 数量多起来,设定方面肯定比较痛苦。如想了解关於 Unicast 设定,可参考本网关於 OSPF 或 EIGRP 的文章。

实验网络设定
以下网络中,假设 R1 和 R2 需要建立 Routing Protocol (本文使用 EIGRP作例子) 交换其 L0 Network,R3 则当成 Internet 上的 Router,只负责 Route 通 192.168.13.0/24 和 192.168.23.0/24。
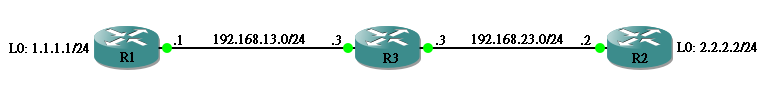
Router 原设定如下:
hostname R1 ! interface Loopback0 ip address 1.1.1.1 255.255.255.0 ! interface Ethernet1/0 ip address 192.168.13.1 255.255.255.0 ! ip route 192.168.23.0 255.255.255.0 192.168.13.3
hostname R2 ! interface Loopback0 ip address 2.2.2.2 255.255.255.0 ! interface Ethernet1/0 ip address 192.168.23.2 255.255.255.0 ! ip route 192.168.13.0 255.255.255.0 192.168.23.3
hostname R3 ! interface Ethernet1/0 ip address 192.168.13.3 255.255.255.0 ! interface Ethernet1/1 ip address 192.168.23.3 255.255.255.0
确定只有 192.168.13.1 能 Ping 通 192.168.23.2。
R1#ping 192.168.23.2 source 192.168.13.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.23.2, timeout is 2 seconds: Packet sent with a source address of 192.168.13.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 20/28/40 ms R1# R1#ping 2.2.2.2 source 1.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 ..... Success rate is 0 percent (0/5)
GRE over IPSec 设定
现在尝试设定 GRE over IPSec,让 R1 及 R2 交换 L0 Network,并使 1.1.1.1 Ping 通 2.2.2.2。
Step 1: 设定 Interesting Traffic
由於目标是把整个 Interface 加密,因此设定以下 ACL。
R1(config)#ip access-list extended IPSEC_TUNNEL R1(config-ext-nacl)#permit ip host 192.168.13.1 host 192.168.23.2
R2(config)#ip access-list extended IPSEC_TUNNEL R2(config-ext-nacl)#permit ip host 192.168.23.2 host 192.168.13.1
Step 2: 设定 IPSec
包括 Phase 1 及 Phase 2 在内的参数已在 IPSec VPN 一文中详述过,不在此重覆。
R1(config)#crypto isakmp key ccie address 192.168.23.2 R1(config)#crypto isakmp policy 10 R1(config-isakmp)#encryption aes R1(config-isakmp)#authentication pre-share R1(config-isakmp)#group 2 R1(config-isakmp)#exit R1(config)#crypto ipsec transform-set TS esp-3des R1(cfg-crypto-trans)#exit R1(config)#crypto map GRE_OVER_IPSEC 10 ipsec-isakmp R1(config-crypto-map)#set peer 192.168.23.2 R1(config-crypto-map)#set transform-set TS R1(config-crypto-map)#match address IPSEC_TUNNEL
R2(config)#crypto isakmp key ccie address 192.168.13.1 R2(config)#crypto isakmp policy 10 R2(config-isakmp)#encryption aes R2(config-isakmp)#authentication pre-share R2(config-isakmp)#group 2 R2(config-isakmp)#exit R2(config)#crypto ipsec transform-set TS esp-3des R2(cfg-crypto-trans)#exit R2(config)#crypto map GRE_OVER_IPSEC 10 ipsec-isakmp R2(config-crypto-map)#set peer 192.168.13.1 R2(config-crypto-map)#set transform-set TS R2(config-crypto-map)#match address IPSEC_TUNNEL
Step 3: 在 Interface 应用 Crypto Map
把以上 IPSec 设定应用到 Interface 之上。
R1(config)#int ethernet 1/0 R1(config-if)#crypto map GRE_OVER_IPSEC
R2(config)#int ethernet 1/0 R2(config-if)#crypto map GRE_OVER_IPSEC
Step 4: 设定 GRE Tunnel
然後在 R1 与 R2 之间开设 GRE Tunnel。
R1(config)#int tunnel 0 R1(config-if)#ip address 172.16.12.1 255.255.255.0 R1(config-if)#tunnel source ethernet 1/0 R1(config-if)#tunnel destination 192.168.23.2
R2(config)#int tunnel 0 R2(config-if)#ip address 172.16.12.2 255.255.255.0 R2(config-if)#tunnel source ethernet 1/0 R2(config-if)#tunnel destination 192.168.13.1
试一下从 172.16.12.1 Ping 到 172.16.12.2,而且成功建立了 IPSec Tunnel。
R1#ping 172.16.12.2 source 172.16.12.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.12.2, timeout is 2 seconds:
Packet sent with a source address of 172.16.12.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/24/36 ms
R1#
R1#show crypto ipsec sa
interface: Ethernet1/0
Crypto map tag: GRE_OVER_IPSEC, local addr 192.168.13.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.13.1/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (192.168.23.2/255.255.255.255/0/0)
current_peer 192.168.23.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 47, #pkts encrypt: 47, #pkts digest: 47
#pkts decaps: 48, #pkts decrypt: 48, #pkts verify: 48
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 192.168.13.1, remote crypto endpt.: 192.168.23.2
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet1/0
current outbound spi: 0x330E2A3(53535395)
PFS (Y/N): N, DH group: none
<--Output Omitted-->
Step 5: 设定 Routing Protocol
最後只需设定 EIGRP 便可。
R1(config)#router eigrp 1 R1(config-router)#no auto-summary R1(config-router)#network 172.16.12.0 0.0.0.255 R1(config-router)#network 1.1.1.0 0.0.0.255
R2(config)#router eigrp 1 R2(config-router)#no auto-summary R2(config-router)#network 172.16.12.0 0.0.0.255 R2(config-router)#network 2.2.2.0 0.0.0.255
这样应可成功建立 Neighbor 并 Ping 通。
R1#show ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(1)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 172.16.12.2 Tu0 12 00:00:48 34 1470 0 4
R1#
R1#ping 2.2.2.2 source 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/22/32 ms
IPSec over GRE 设定
现在把设定回复至实验初始状态,今次尝试设定 IPSec over GRE,让 R1 及 R2 交换 L0 Network,并使 1.1.1.1 Ping 通 2.2.2.2。
Step 1: 设定 GRE Tunnel
先建立 GRE Tunnel。
R1(config)#int tunnel 0 R1(config-if)#ip address 172.16.12.1 255.255.255.0 R1(config-if)#tunnel source ethernet 1/0 R1(config-if)#tunnel destination 192.168.23.2
R2(config)#int tunnel 0 R2(config-if)#ip address 172.16.12.2 255.255.255.0 R2(config-if)#tunnel source ethernet 1/0 R2(config-if)#tunnel destination 192.168.13.1
确定 GRE 能 Ping 通,留意现时未有加密。
R1#ping 172.16.12.2 source 172.16.12.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.12.2, timeout is 2 seconds: Packet sent with a source address of 172.16.12.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 20/22/32 ms
Step 2: 设定 Routing Protocol
R1(config)#router eigrp 1 R1(config-router)#no auto-summary R1(config-router)#network 172.16.12.0 0.0.0.255 R1(config-router)#network 1.1.1.0 0.0.0.255
R2(config)#router eigrp 1 R2(config-router)#no auto-summary R2(config-router)#network 172.16.12.0 0.0.0.255 R2(config-router)#network 1.1.1.0 0.0.0.255
现时 1.1.1.1 已可 Ping 通 2.2.2.2,但未被加密。
R1#show ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(1)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 172.16.12.2 Tu0 14 00:04:07 67 1470 0 6
R1#ping 2.2.2.2 source 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/21/28 ms
Step 3: 设定 Interesting Traffic
由於目标是把 Data 加密,即由 1.1.1.1 至 2.2.2.2,因此设定以下 ACL。
R1(config)#ip access-list extended IPSEC_TUNNEL R1(config-ext-nacl)#permit ip host 1.1.1.1 host 2.2.2.2
R2(config)#ip access-list extended IPSEC_TUNNEL R2(config-ext-nacl)#permit ip host 2.2.2.2 host 1.1.1.1
Step 4: 设定 IPSec
IPSec 设定跟之前 GRE over IPSec 相若,只是 Peer IP 不同,因现在 IPSec 建在 GRE Tunnel 之上,双方 Peer 应该是 172.16.12.1 和 172.16.12.2。
R1(config)#crypto isakmp key ccie address 172.16.12.2 R1(config)#crypto isakmp policy 10 R1(config-isakmp)#encryption aes R1(config-isakmp)#authentication pre-share R1(config-isakmp)#group 2 R1(config-isakmp)#exit R1(config)#crypto ipsec transform-set TS esp-3des R1(cfg-crypto-trans)#exit R1(config)#crypto map IPSEC_OVER_GRE 10 ipsec-isakmp R1(config-crypto-map)#set peer 172.16.12.2 R1(config-crypto-map)#set transform-set TS R1(config-crypto-map)#match address IPSEC_TUNNEL
R2(config)#crypto isakmp key ccie address 172.16.12.1 R2(config)#crypto isakmp policy 10 R2(config-isakmp)#encryption aes R2(config-isakmp)#authentication pre-share R2(config-isakmp)#group 2 R2(config-isakmp)#exit R2(config)#crypto ipsec transform-set TS esp-3des R2(cfg-crypto-trans)#exit R2(config)#crypto map IPSEC_OVER_GRE 10 ipsec-isakmp R2(config-crypto-map)#set peer 172.16.12.1 R2(config-crypto-map)#set transform-set TS R2(config-crypto-map)#match address IPSEC_TUNNEL
Step 5: 在 Tunnel Interface 应用 Crypto Map
最後把以上 IPSec 设定应用到 Tunnel Interface 之上。
R1(config)#int tunnel 0 R1(config-if)#crypto map IPSEC_OVER_GRE
R2(config)#int tunnel 0 R2(config-if)#crypto map IPSEC_OVER_GRE
R1#ping 2.2.2.2 source 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 40/41/44 ms
R1#
R1#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: IPSEC_OVER_GRE, local addr 172.16.12.1
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (2.2.2.2/255.255.255.255/0/0)
current_peer 172.16.12.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 172.16.12.1, remote crypto endpt.: 172.16.12.2
path mtu 1476, ip mtu 1476, ip mtu idb Tunnel0
current outbound spi: 0xBC0A1C2(197173698)
PFS (Y/N): N, DH group: none
<--Output Omitted-->
相關主題
Jan Ho 2021-07-22
Posted In: menu-tall-2-zh-hans, 虚拟私人网路 VPN
发表回复